Computer Components and Evidence
A computer is actually composed of a number of different parts, which are joined together to make the overall system. Each of these parts plays an important role in the operation of the computer, but not each part will contain useful digital forensic evidence. In this lesson, we will look at which parts of the computer system are most likely to contain evidence that will be useful in a digital forensic investigation.
It is important to note that the evidence utility described here refers exclusively to digital evidence. Such evidence is stored in the form of data inside the computer. While some components, such as the computer case, are unlikely to contain digital forensic evidence, they are likely to contain physical forensic evidence. Physical evidence, such as fingerprints and DNA, are outside the scope of digital forensic practice.
Video Lecture
The Case
The computer case (Figure 1) is the shell that contains the rest of the components. It protects and organizes the internal components, shields them from outside electrical interference, and promotes cooling by directing airflow and radiating heat. Cases themselves are not usually a source of digital evidence, but they are likely sources of physical evidence, such as fingerprints or DNA.

Cases are available in a wide variety of form factors, shapes, and sizes. When performing evidence discovery, such as a search at a crime scene, it is important to recognize that computers do not necessarily have one standard appearance. While most people are familiar with traditional desktops and laptops, there are many other form factors available. Examples include rackmount servers, ultra small form factor (USFF) computers, and single-board computers (such as the Raspberry Pi1). Furthermore, it is possible to design and build fully custom computer cases in any shape or size, potentially concealing the existence of the computer within.
It is also important to recognize that computer cases can be fitted with intrusion detection switches, which activate whenever the case is opened. Other types of switches may be fitted, which activate whenever the computer system is moved or otherwise disturbed. These switches may be wired to trigger a data destruction process when activated, destroying any digital evidence stored on the computer system. Worse, these switches could be wired to explosive or incendiary devices that physically destroy the computer system and may seriously injure or kill an investigator.
The Power Supply Unit (PSU)
Unless powered directly by DC voltage, computer systems contain a power supply unit or PSU. This device converts AC mains electrical power to the low-voltage DC power that is used by the computer’s internal components. A PSU may be internal (Figure 2) or external. Consumer-grade PSUs are not typically sources of digital forensic evidence, since they do not contain internal storage. However, the PSU may still contain fingerprints and other physical evidence, especially if it is the external variety (brick or wall wart).

Enterprise PSUs, such as the ones found in rackmount servers, are a potential (if unlikely) source of digital forensic evidence. These devices may contain firmware that can be upgraded in the field, which means they contain internal storage. It is at least theoretically possible for such a PSU to serve as a malware vector, and sophisticated malware (or an extremely sophisticated user) might implant data into the PSU onboard storage. Should you encounter an enterprise server, check the manufacturer’s website for updates to the power supply, which would indicate the presence of firmware and storage within this device.
The Motherboard and CPU
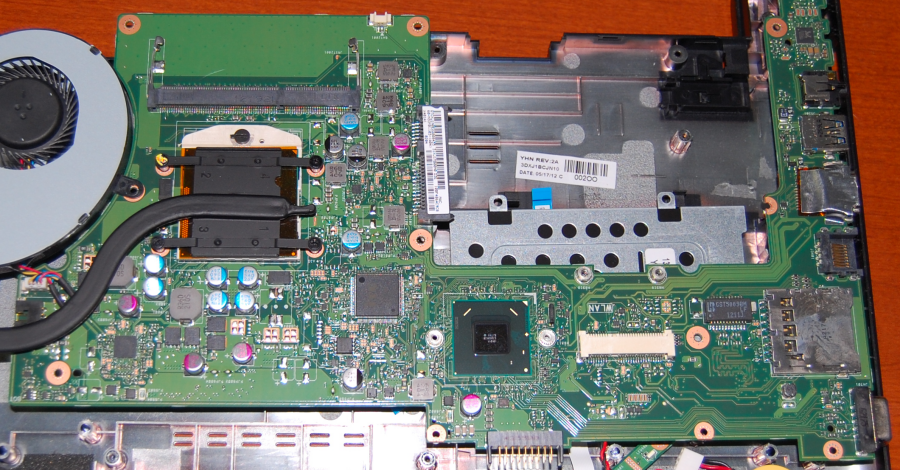
Inside the case, the motherboard is the main circuit board that connects the central processing unit (CPU), memory, and other internal components together to form a complete computer system. The CPU is normally concealed beneath a heat sink (on a desktop computer) or heat pipe (laptop), which helps cool the processor. Figure 3 shows a laptop motherboard with a heat pipe covering the CPU.
Motherboard
It is possible for the motherboard itself to contain digital evidence. Direct digital evidence might be found in the programmable flash storage chip that contains the Unified Extensible Firmware Interface (UEFI) or Basic Input-Output System (BIOS) code that is responsible for booting the computer. Malware may infect this chip, and a sophisticated user with the correct tools can embed arbitrary data inside the chip.
Enterprise motherboards normally contain a separate out-of-band management controller, such as a Dell iDRAC, HP iLO, or Intel AMT/vPro controller. These devices are essentially separate computers connected to the motherboard, which normally have separate network interfaces for performing remote system administration on the computer. An insecure management controller may permit a remote attacker to access a server. Furthermore, the management controller itself could become a source of digital forensic evidence if malware or a sophisticated individual manages to inject data into the management controller firmware.
In addition to direct evidence, most motherboards have a real-time clock (RTC) component that is responsible for storing system time when the computer is in the powered off state. The time setting from the RTC is useful in a forensic investigation to determine if the system time was set accurately whenever files were created, accessed, or updated.
Another key piece of indirect evidence is the configuration of components that are connected to the motherboard. Before disconnecting any cable, or removing any device from a slot or connector, take a photograph, and document which components were connected to which ports or interfaces. This information establishes the topology of the computer, and it may prove to be important in a later investigation.
CPU
The central processing unit contains internal memory in the form of caches and registers that are used in high speed computations. As such, the contents of these memories may contain digital forensic evidence. However, accessing data in the CPU cache or in registers is not especially practical for a forensic examiner. These memory locations are volatile and will be cleared whenever the CPU loses power or is reset (such as during reboot). Thus, only special live acquisition tools have any real chance of recovering data directly from the CPU, and recovery would only be possible to the extent that the live acquisition tool itself does not overwrite the evidence when writing the tool’s machine code into the CPU for execution.
Random Access Memory (RAM)
Random Access Memory (RAM) is short-term memory that is used to store data while the computer is running. This memory is much faster than persistent storage, but it is volatile, meaning that its contents are lost whenever power is removed. Discrete RAM chips come in desktop (Figure 4) and laptop module sizes. Some newer laptops have their RAM modules permanently soldered to the motherboard, while small embedded and single-board systems normally have RAM that is part of the main CPU chip (system on a chip, or SOC).

RAM frequently contains digital forensic evidence. However, since it is volatile, any such evidence is lost whenever power to the computer is turned off. In theory, it is possible to recover some evidence from RAM if the chips can be removed from the computer quickly and cooled.2 Other types of cold boot attacks have been demonstrated without removal of the RAM, but they require special tools to prevent the system from overwriting the contents of RAM during a forced reboot.3
Apart from a successful cold boot attack, the other way to recover data from RAM is to use a live acquisition tool that runs on the target computer and dumps the contents of RAM to portable evidence storage. The success of such a tool depends upon the ability of the tool to access memory quickly and without restrictions. Furthermore, the investigator must have access to the target system to run the tool in the first place. Such access can be denied by a simple screen locking program.
Network Adapters

Most modern computers have a network adapter, or network interface card (NIC). This adapter may be built into the motherboard or may appear as a separate card that plugs into a slot or connector on the motherboard. Both wired and wireless adapters are found in many modern systems, and these adapters enable each system to connect to a network, which in turn may permit connection to the Internet.
Network forensics, in general, happens outside the scope of the network adapter. However, network adapters are programmable, and many of them do contain flash memory. It is therefore possible for a piece of malware or a sophisticated user to store a small amount of evidence on the adapter. In practice, however, we normally regard network adapters as volatile devices, losing any useful data once the computer is turned off.
That said, network adapters are important pieces of indirect evidence. In particular, the media access control (MAC) address of a network adapter might be useful for linking the adapter to a network connection or to a set of intercepted data. If a network capture is performed, and no encryption is in use, readable evidence may be present in this data set. With or without such a capture, a MAC address might be used to link a computer to an Internet address, which might then link the computer to some specific online activity.
Note that I must emphasize that the MAC address only links the adapter to an activity. It is still necessary to show that the adapter was in the computer at the time (which is easy to do when the adapter is soldered to the motherboard). Furthermore, it is necessary to show that a given user was using the computer at the time of the questionable activity, and that another user wasn’t responsible for the activity.
It is extremely important to note that MAC addresses are easily spoofed. A third party can steal the MAC address from an adapter and pretend to be the party that owns the device with that MAC address. Such theft does not require access to the device itself, particularly when using insecure public, convention, airport, or hotel wireless Internet. Simple scanning tools would permit an attacker to discover the MAC address of another device.
In addition, it is possible for the user, or for the computer operating system, to change the MAC address to a random address before making a connection. Some collisions between randomly selected addresses and “real” addresses used by hardware would be expected with this approach. Both Tails4 and iOS 145 are known to support using randomized MAC addresses in an easy-to-use fashion. Any user with intermediate to advanced computer skills can change their own MAC address with relative ease.
Persistent Storage
By far, the largest source of digital forensic evidence in a computer will be found in its persistent storage devices. These devices are intended for long-term storage of data, and are therefore non-volatile. In general, persistent storage devices can be removed from a computer and imaged, and then an analysis can be performed on the image to locate relevant evidence.
These devices are normally connected to the computer’s motherboard via a cable, connector, or slot. For most devices, a cable is used. However, some newer motherboards have connectors for solid state drive (SSD) or embedded multimedia card (eMMC) devices. It is also possible, especially in the case of embedded systems such as mobile phones, for an eMMC to be soldered directly to the motherboard.
Many types of storage devices exist, and devices may be located inside the computer case (internal devices) or outside the case (external devices). Hard drives, SSDs, eMMCs, secure digital (SD) cards, USB flash drives, optical discs, and tape drives are just some of the storage media that might contain evidence. Some of these devices are tiny and easily hidden, making them difficult to find.
Hard Disk Drives

A hard disk drive (HDD) (Figure 6) is a mechanical contraption that stores data on metal or metal-coated glass platters. The platters spin around at high speed, and a stack of drive heads moves in and out across the platters, allowing data to be read or written using magnetism. Compared to the CPU and RAM, hard drives are incredibly slow. However, they are inexpensive, and models are readily available that can store multiple terabytes (TB) of digital evidence.
Solid State Drives
As shown in Figure 7, a solid state drive (SSD) is a non-mechanical device that stores data in flash memory cells. These devices are significantly faster than hard drives, but they cost more. Capacities of several TB are commercially available, and these devices may contain the same types of digital evidence as hard drives.
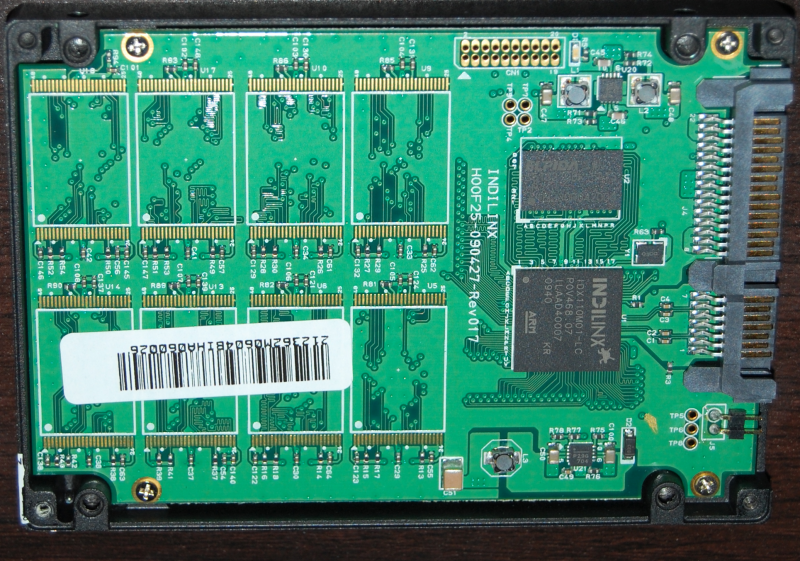
Compared to hard drives, SSDs present several additional challenges to a forensic investigator. First, special evidence handling techniques are needed to retrieve the data from these devices without accidentally changing or deleting (spoliating) the evidence. Second, the solid state memory inside an SSD eventually leaks out the electrons that it contains, resulting in data loss. If an SSD is stored for an extended period of time, degradation of the digital evidence will occur.
Other Media
Other media devices may contain digital evidence. For example:
- Optical discs (CD, DVD, Blu-ray) may contain digital evidence. There is a slight possibility that optical drives, most of which contain some firmware, could contain evidence. However, most of the evidence would likely be found in the disc and not the drive.
- Tape drives are used in enterprise settings. These devices frequently have embedded firmware and could be targeted by malware, hackers, or advanced users. However, as is the case with optical discs, most of the digital evidence is likely to be stored on the tapes, typically in the form of backups.
Peripheral Devices
Peripheral devices to a computer include the keyboard, mouse, camera, printer, scanner, and a whole host of other pieces of hardware. These devices might prove useful for connecting the user to the computer, or they might show that the user had the ability to take some action using the computer. As a result, these devices can be valuable sources of both physical forensic evidence and indirect digital evidence.
Some peripherals, including advanced gaming keyboards and printers, contain firmware and embedded flash storage. A piece of malware or an advanced user might be able to store arbitrary data inside these devices. It is therefore possible for peripherals to contain direct digital evidence.
Notes and References
-
J. Alex Halderman, et al. Lest We Remember: Cold-Boot Attacks on Encryption Keys. Communications of the ACM 52(5), 91-98, 2009. ↩
-
F-Secure. The Chilling Reality of Cold Boot Attacks. YouTube. 2018. ↩
-
Use private Wi-Fi addresses in iOS 14, iPadOS 14, and watchOS 7 ↩
