Disk Imaging
Perhaps the greatest sources of evidence in most forensic investigations are the storage devices used by the subject of the investigation. It is therefore necessary for the forensic examiner to review the contents of these devices to look for evidence. However, we must be careful that we don’t change the evidence in any way during the collection process.
To prevent changes, we make a bitstream image of each storage device, which is a low-level duplicate copy of all the data and data structures used on the device. We create this image using a write blocker to reduce the chances of introducing changes to the original evidence. Immediately after collecting the image, we hash the image to obtain its fingerprint, so that we can verify that no later analysis operations are creating false evidence.
Video Lecture
Evidence Integrity and Acquisition
Data on a computer system or another digital device are easily altered or deleted, making the evidence these devices contain relatively fragile. If alteration of the data should occur during the process of carrying out a forensic investigation, the conclusions drawn from the investigation may be faulty. Changes to evidence may result in spoliation, which is the legal term for evidence that has been damaged or altered. Spoliated evidence is likely to be found to be inadmissible in court, making the whole forensic examination useless if it is not carried out correctly.
The standard way to handle digital evidence is to make a copy of the original storage medium, without changing the original device. All analysis and investigation is performed on the resulting copy and never on the original storage medium. When performed correctly, another investigator should be able to obtain an identical copy from the original storage device later, proving the original device has not been changed.
Storage Devices and Space Allocation
There are a multitude of different storage devices that might contain evidence, and new storage technology is constantly being developed. For much of the time that digital forensics has existed as a field, the hard disk drive (Figure 1) has been the primary storage device for large amounts of potential evidence. Hard drives are mechanical devices that store information magnetically.

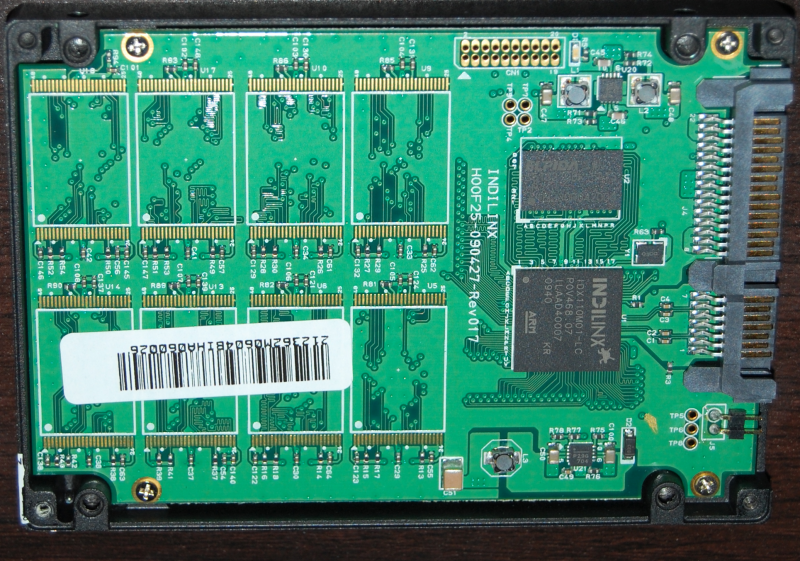
In recent years, solid state drives (SSDs) have replaced hard disk drives in many laptops, desktops, and workstations. SSDs (Figure 2) store information using solid-state microchips, using a storage technology called flash memory.
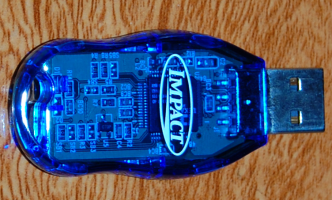
Flash memory is also used in portable storage devices, including USB drives (Figure 3) and various kinds of memory cards. As of mid-2022, one of the more popular types of memory card is the microSD card, which can store a significant amount of data on a device that is only 11x15x1 mm in physical size1, or about the size of a human fingernail.
Other types of storage devices also exist. Optical discs, such as CD, DVD, and Blu-ray, were once popular devices for removable storage. Writable and re-writable versions are still commercially available as of mid 2022, although flash drives and the use of Internet storage services have eclipsed these devices in terms of popularity. Prior to the advent of optical drives, portable magnetic storage media was common, including floppy disks.
At the enterprise level, tape drives are commonly used for long term retention of computer backups and other slowly-changing types of data. While these devices are not common in consumer applications (largely due to their expense), backups of server systems and other corporate and institutional computers may use these devices. Consequently, tape drives may contain evidence that a subject might have erased from a system since the time a backup was made.
Partitions
Hard disks, solid state drives, flash drives, memory cards, and many other types of storage devices are typically divided into different storage regions, or partitions. As illustrated in Figure 4, partitions can be used to isolate different storage areas from one another on a device. With older and slower mechanical storage devices, separating the device into multiple partitions could also improve performance for some workloads. As far as a typical computer operating environment is concerned, each partition appears to be a separate logical storage device.
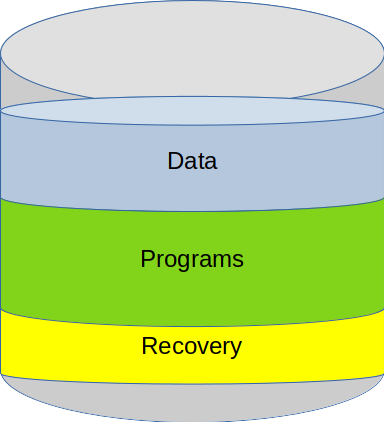
When partitions are used, not all parts of a drive are necessarily allocated to a partition. Unallocated space commonly is found at the start and end of a drive, but it may occur anywhere within a storage device. An unallocated mebibyte (or binary megabyte: 1,048,576 bytes) nearly always occurs at the beginning of every storage device for performance reasons, as it allows all the partitions on the device to be aligned in a way that makes access more efficient by modern hardware.
Evidence may be lurking in these unallocated spaces, since tools exist that can store data into these regions. In digital forensics, these unallocated areas are a type of slack space, or a part of the device into which data are not normally written.
Bitstream Imaging and Alternatives
Since evidence might be located in slack space on the storage device, we need to be able to examine every area of the device. At the same time, we must not risk changing the original device itself. In order to do this low-level analysis, we need to create an exact copy of each and every bit present on the device. This low-level copy is called a bitstream image of the original.
In addition to permitting examination of the slack space, a bitstream image also provides access to deleted files from parts of the storage device that have not yet been physically erased or overwritten with new data. Forensics tools can be used to search for deleted files, potentially recovering the evidence they might contain. The primary downsides to bitstream images are that they can be slow to acquire and expensive to store, since a case might involve numerous storage devices, each of which could be hundreds of gigabytes or even terabytes in size.
While it would take a lot less space and be less cumbersome to analyze the evidentiary device and only copy the parts that are relevant to the investigation, this approach is not generally acceptable in court. Merely copying files does not usually preserve useful metadata, such as owner, creation time, modification time, etc. Searching through the evidentiary device to look for important data creates opportunities to modify it, damaging the evidence and risking inadmissibility.
The National Institute of Justice has been funding acquisition tools that selectively image only parts of storage devices that contain interesting data, skipping segments containing programs and other irrelevant material. As storage devices grow larger, NIJ expects this process to speed up evidence processing time to reduce forensic examination backlogs.2
Fingerprinting Images (Hashing)
After creating a disk image, it is standard procedure to collect a cryptographic hash of the resulting image file. This hash is used as a fingerprint to verify that the image file isn’t accidentally changed during the forensic analysis of the image. A second investigator should get the same fingerprint if another image is created from the same storage device.
Read-Only Imaging and Write Blocking
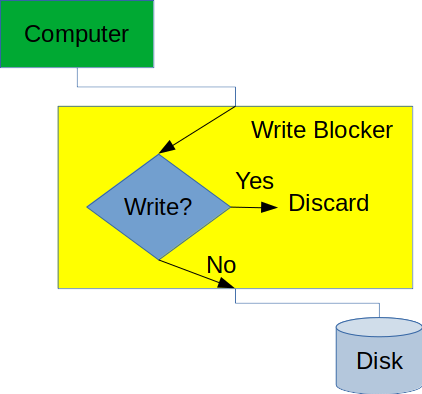
It is critical that the underlying storage device is not changed in any way during a forensic analysis, as changing the original evidence may result in a court suppressing it. Several techniques exist for preventing changes, but one standard procedure is to use a hardware write blocker when collecting the bitstream image. A write blocker is a special device that is connected to the forensics workstation at one end and to the device to be imaged at the other. It permits commands that read data from the device to be executed, while blocking those that might result in changes to the device, as shown in Figure 5.
While the use of a write blocker is a standard procedure in an investigation, it isn’t a foolproof way to guarantee that the original device will not be changed as a result of the investigation. This is especially true when imaging solid state drives and other flash memory devices, as we will see later.
Notes and References
-
SD Association. SD Standard Overview. ↩
-
Martin Novak, Jonathan Grier, and Daniel Gonzales. “New Approaches to Digital Evidence Acquisition and Analysis.” National Institute of Justice. October 7, 2018. https://nij.ojp.gov/topics/articles/new-approaches-digital-evidence-acquisition-and-analysis ↩
Further Reading
- Sally Vandeven. “Forensic Images: For Your Viewing Pleasure.” SANS GIAC Cybersecurity Certification paper, 2014.
- U.S. Department of Justice, National Institute of Justice. Digital Evidence in the Courtroom: A Guide for Law Enforcement and Prosecutors. NIJ Special Report. January 2017.
- U.S. Department of Justice, National Institute of Justice. Forensic Examination of Digital Evidence: A Guide for Law Enforcement. NIJ Special Report. April 2004.
