Forensic Hardware
Various vendors have developed special-purpose hardware for performing digital investigations. While a thorough review of all available devices would require a course unto itself, two classes of forensic hardware are especially common: write blockers and mobile device tools. Write blockers are general-purpose devices that are intended to reduce the chances of evidence spoliation while acquiring an image from a storage device. Mobile device tools, including acquisition units and Faraday bags or cages, provide a means to secure and retrieve evidence from cell phones.
Video Lecture
Write Blockers
When acquiring an image of a disk drive, it is a forensic best practice to place a hardware write blocker (Figure 1) between the drive and the forensic lab computer that is being used for the acquisition. Failing to use a write blocker may result in spoliation of the evidence, since the operating system could send commands to the drive that alter the state of the storage. A write blocker, as its name implies, prevents such commands from being passed through to the drive, reducing the risk of changing its contents.
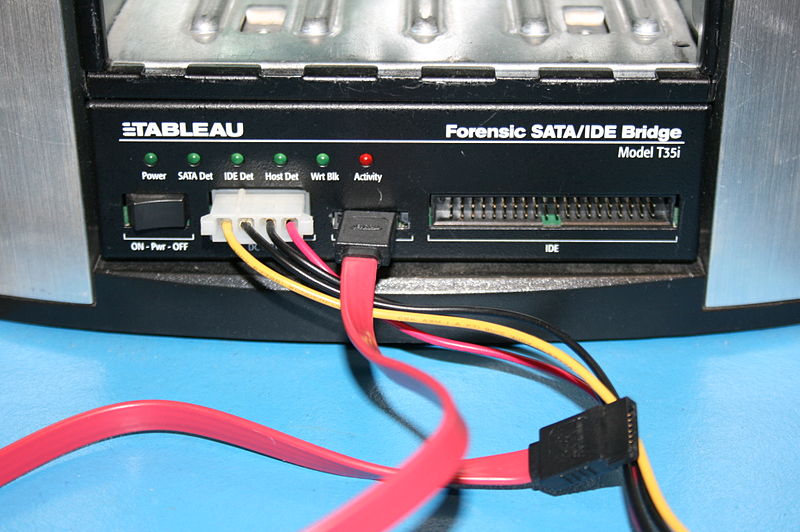
Note that a hardware write blocker does not guarantee that the contents of the drive won’t be changed during the image acquisition process. Modern drives are capable of storing previously issued commands, even if power to the drive is removed. Once power to the drive is restored, the drive may execute the stored commands, potentially changing or deleting evidence. Solid state drives, along with other flash memory devices, may perform background data erase operations as a way of improving performance. Erases that were scheduled before power was cut to the drive may resume automatically when power is restored to the drive. Since these operations are performed by the drive’s embedded firmware, a write blocker will do nothing to prevent them from occurring.
Mobile Device Acquisition
Mobile devices – cell phones, in particular – require special handling in order to retrieve evidence stored on them. Special-purpose acquisition tools (Figure 2) are usually needed to image mobile devices and obtain a copy of the data on them. These tools normally require plugging the phone into the tool, which then uses a device-specific recipe for accessing the data.

There is normally a delay from the time that a mobile device is seized in an investigation to the time at which its evidence is acquired. During this delay, there is a chance that the suspect will send a remote wipe command to the phone, destroying any evidence it contains. This threat is reduced by placing the phone inside a Faraday cage or bag (Figure 3) at the time of its initial seizure. A fine metal mesh surrounds the phone, blocking any radio signals from entering or leaving the device.

Of course, nothing is foolproof. A sophisticated user could install a phone app that senses a complete loss of radio signals and immediately locks or wipes the device. Similarly, a software-based trigger can be added that causes immediate data destruction if the phone is connected to an acquisition device. Moreover, some newer phones automatically lock the USB connector and refuse to permit an external device to connect unless the user enters a password or performs another unlock operation.4
