Darknets
In modern usage, a darknet is a networks built on top of the Internet, which typically requires special software to access. Historically, the term “darknet” originated in the 1970s to describe secure defense networks and devices attached to ARPANET, which could receive data from ARPANET but would not reply or otherwise acknowledge their existence.1
Video Lecture
Uses of Darknets
Darknets, which collectively are sometimes grouped together as the so-called Dark Web, have a number of legitimate uses. Security, intelligence, and counterintelligence operations still take place in these hidden online systems, echoing the original meaning of the term darknet. Reporters and journalists can make use of darknets to receive whistleblower complaints, information leaks, and other types of news securely, with minimal risk to the source. These overlay networks can improve the security, privacy, and anonymity of their users, making them beneficial to victims of cyberstalking, online harassment, and human rights violations. Security researchers are able to use darknets for a variety of purposes, including gathering information on exploits, hacker groups, and other potential threats.
As is the case with any technology, darknets also have a dark side. Illegal activities do take place inside these systems. Hidden markets exist for all types of illicit goods, including drugs, weapons, and stolen financial information. Criminals may offer services such as identity theft, regular theft, hacking, kidnapping, and murder. Internationally, criminals may use darknet sites to organize, sharing extremist propaganda, child abuse material, or animal abuse material. Jilted lovers might use a darknet to share revenge porn.
Darknets in Popular Media
The illegal activities that take place on darknets yield far more sensationalist news stories than do the legal activities, so news reports about darknets tend to look unfavorably upon these systems, carrying headlines such as: “Study Claims Dark Web Sites Are Most Commonly Used for Crime.”2 Based on an academic study of Tor hidden sites (a type of darknet), illegal content was found on approximately 20% of the sites surveyed (see Figure 1). This percentage, while high, falls short of “most commonly.”
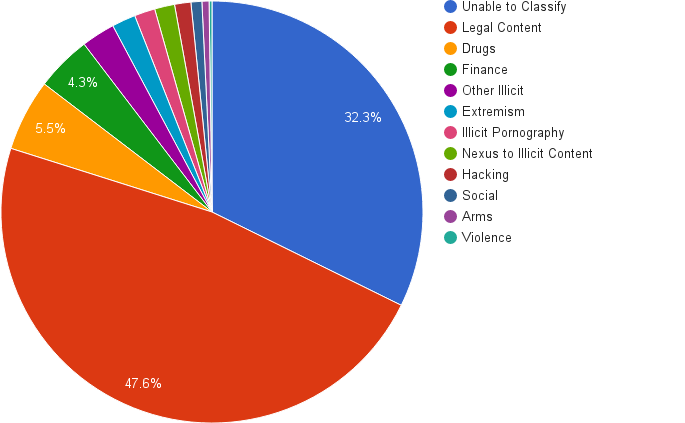
Included within the definition of “illegal” content on the darknet are sites that simply link to other sites, where the other sites actually contain illegal material. Such sites serve as a “nexus” to illegal content, making such content easier to find.4
Law Enforcement in Darknets
One difficulty in addressing illegal content in darknets is that law enforcement must first identify the location of the server hosting the content before it can be removed. Utilizing various techniques, including infiltrating criminal organizations and hacking into servers, law enforcement organizations occasionally do manage to take down illegal hidden sites. However, new sites appear as quickly as old ones are removed.
Some of the techniques used to take down an illegal website are otherwise illegal themselves. For example, an FBI Network Investigative Technique (NIT) might require infecting a hidden site with malware or otherwise compromising the site. Such actions, if undertaken by private individuals outside the protections of government, would be crimes themselves. A particularly egregious example of a questionable FBI action against a hidden site occurred between February 20, 2015, and March 4, 2015, during which time the FBI knowingly distributed child sexual abuse material in a somewhat dubious attempt to try to catch users of the hidden site.5
Accessing Darknet Sites
In order to access darknet sites, special software is required. The exact software needed depends upon the system to be accessed. Tor hidden services, which constitute the largest and most widely used darknet, require the investigator to use the Tor client.6 Smaller darknets include “Eepsites” reachable only via the Invisible Internet Project (I2P)7 and Freenet8, which has its own client.
Various directories of hidden sites exist, some of which are available on the “clearnet,” or regular Internet, such as Hidden Wiki9 (not to be confused with the darknet site of the same name) and OnionLink10. Extreme caution must be used in accessing darknet sites, as the content on a site may not match its description. Illegal, offensive, and malicious content may be encountered in darknet systems. The use of a high security environment such as Tails11 may mitigate some of the risk, but conducting any investigation or research using a darknet system may expose the investigator to unwanted content.
Notes and References
-
Darknet History August 21, 2017. ↩
-
Joseph Cox. “Study Claims Dark Web Sites Are Most Commonly Used for Crime.” Vice. February 1, 2016. Article ↩
-
Data Source: Daniel Moore and Thomas Rid. “Cryptopolitik and the Darknet.” Survival 58(1): 7-38, 2016. ↩
-
Daniel Moore and Thomas Rid. “Cryptopolitik and the Darknet.” Survival 58(1): 7-38, 2016. Publisher Site ↩
-
Mary-Ann Russon. “FBI crack Tor and catch 1,500 visitors to biggest child pornography website on the dark web.” International Business Times. January 7, 2016. Article Note: Despite the headline, the FBI did not actually “crack Tor.” ↩
